Overview
Who Should Attend
This course is designed for anyone seeking an active role in the field of information security. The job roles best suited to the material in this course are:
Information Security Analysts / Administrators / Auditors who manage and analyse an organisation’s security posture
Information Security / SOC / VAPT / Cloud professionals responsible for protecting and securing critical information and systems
Information Security Incident Responders / Threat Hunters / Application Security / Web Application Penetration Testers
Information Security SIEM Responders / End Point Security / SOAR Engineers / AI Security Engineers / Exploitation Analysts
Information Security Zero Trust Solutions Engineers / Cryptographic Engineers / AI/ML Security Engineers / AI Penetration Testers
What's In It for Me
New Industry Benchmark – 5 Phases of Ethical Hacking Framework + AI
AI-Driven Cybersecurity Skills (40% more efficiency in cyber defense, 90% accuracy in detecting various cybersecurity threats)
Master How to Use AI Skills
Learn to Hack AI Systems
Learn Multiple AI and GPT Tools
AI and Machine Learning in Cybersecurity
Skills Learned in the CEH Are Mapped to 49 Cybersecurity Job Roles (increased from 20 to 49)
AI-Driven Ethical Hacking, Zero Trust Architecture, Active Directory Attacks, Ransomware Attacks and Mitigation, Cloud Security, AI and Machine Learning in Cybersecurity, IoT Security Challenges, Critical Infrastructure Vulnerabilities, Deepfake Threats, Extended Detection and Response (XDR), Quantum Computing Risks and Attacks, Post-Quantum Cryptography
Course Overview
The EC-Council Certified Ethical Hacker (CEH) v13 is a cutting-edge program that integrates AI-driven cybersecurity skills and a 5-Phase Ethical Hacking Framework to enhance threat detection and defense efficiency. This updated course covers AI and machine learning in cybersecurity, teaching participants to hack AI systems, use AI tools, and mitigate advanced threats like ransomware, deepfakes, and quantum computing risks. With skills mapped to 49 cybersecurity job roles, CEH v13 prepares professionals for roles such as Penetration Tester, Security Consultant, and Cloud Security Specialist, equipping them with hands-on experience in AI, Zero Trust Architecture, IoT, and critical infrastructure security.
Course Description & Learning Outcomes
Course Objectives
Upon completing the course, students will be able to:
Carry out threat modelling and secured source code review
Conduct authorised penetration testing of systems using various methodologies, tools and techniques
Use network monitoring and vulnerability scanning tools to assess threats and vulnerabilities
Identify vulnerability exploitations and potential attack vectors
Analyse vulnerability scan results to assess security loopholes and threats
Evaluate if systems can overcome emerging threats and hacking techniques such as Deepfake threats
Identify Active Directory attacks and critical infrastructure vulnerabilities
Develop a vulnerability assessment and penetration testing report, highlighting key threats and areas for improvement
Understand processes and techniques for secured source code review
Understand ransomware attacks and mitigation
Apply penetration testing techniques and methodologies
Understand Extended Detection and Response (XDR)
Understand AI and Machine Learning in cybersecurity
Understand quantum computing risks and threats
Identify IoT security challenges
Course Outline
Module 01: Introduction to Ethical Hacking
Module 02: Footprinting and Reconnaissance
Module 03: Scanning Networks
Module 04: Enumeration
Module 05: Vulnerability Analysis
Module 06: System Hacking
Module 07: Malware Threats
Module 08: Sniffing
Module 09: Social Engineering
Module 10: Denial-of-Service
Module 11: Session Hijacking
Module 12: Evading IDS, Firewalls, and Honeypots
Module 13: Hacking Web Servers
Module 14: Hacking Web Applications
Module 15: SQL Injection
Module 16: Hacking Wireless Networks
Module 17: Hacking Mobile Platforms
Module 18: IoT Hacking
Module 19: Cloud Computing
Module 20: Cryptography
Certificate Obtained and Conferred by:
Certificate of Completion from NTUC LearningHub
Upon meeting at least 75% attendance and passing the assessment(s), participants will receive a Certificate of Completion from NTUC LearningHub.
Statement of Attainment (SOA) from SkillsFuture Singapore
After passing the assessment(s), participants will receive a SOA from SkillsFuture Singapore, certifying that they have achieved the following Competency Standard(s):
ICT-DIT-3012-1.1 Security Assessment and Testing-3
External Certification
The participant will be able to attempt the Certified Ethical Hacker (ANSI) Certification Exam after attending this course. Upon passing the exam, you will receive the Certified Ethical Hacker (ANSI) Certificate. This certification credential is trusted globally as the industry standard for evaluating one’s understanding of ethical hacking and security testing. As an ANSI 17024 accredited examination, the 150-question, 4-hour proctored exam is recognized across the globe as the original and most trusted tactical cyber security certification for ethical hackers. For more information on the exam and coverage refer to EC-Council website: <html> <body> <!--StartFragment-->https://cert.eccouncil.org/certified-ethical-hacker.html<!--EndFragment--> </body> </html>
As part of the CEH Elite package, the CEH Practical Exam voucher is also included in the learning kit. C|EH Practical is a 6-hour, rigorous exam that requires you to demonstrate the application of ethical hacking techniques such as threat vector identification, network scanning, OS detection, vulnerability analysis, system hacking, web app hacking, etc. to solve a security audit challenge. This is the next step after you have attained the highly acclaimed Certified Ethical Hacker certification. Professionals that possess the C|EH credential will be able to sit for exam that will test them to their limits in unearthing vulnerabilities across major operating systems, databases, and networks. You will be given limited time, just like in the real world. The exam was developed by a panel of experienced SMEs and includes 20 real-life scenarios with questions designed to validate essential skills required in the ethical hacking domains as outlined in the C|EH program, more information here: <html> <body> <!--StartFragment-->https://cert.eccouncil.org/certified-ethical-hacker-practical.html<!--EndFragment--> </body> </html>
External Certification Exam
The course fee includes the C|EH® (ANSI) certification exam fee for trainees who attend and complete the EC-Council Certified Ethical Hacker (CEH) course with NTUC LearningHub.
For students who require re-take, 1 re-exam voucher is included in the student learning kit. For subsequent re-take attempts, the C|EH® (ANSI) certification exam voucher can be purchased at the full fee from our Exam e-shop on our website here: <html> <body> <!--StartFragment-->Exam e-shop<!--EndFragment--> </body> </html>
Or you can contact us at <html> <body> <!--StartFragment-->[email protected]<!--EndFragment--> </body> </html>
Recommended Prerequisites
Pre-requisites:
The admission requirements are:
You should have some foundational knowledge and skills in network security and IT.
While there are no formal prerequisites for CEH certification, you should demonstrate a good understanding of the exam topics and some familiarity and/or experience in information security.
It is recommended that you have prior formal training in the following:
CompTIA A+
CompTIA Network+
CompTIA Security+
EC-Council Certified Network Defender (CND) (SF)
Recommended for Career Path Advancement
EC Council Computer Hacking Forensic Investigator (CHFI) (For Incident Response and Forensics)
EC Council Certified Incident Handler (ECIH) (For Incident Response and Forensics)
EC Council Certified SOC Analyst (CSA) (For SOC Operations)
Cisco CCNA Cyber Security Operations (For SOC Operations)
ISC2 Certified Information Systems Security Professional (CISSP) (For Security Engineer)
Certificate of Cloud Auditing Knowledge (CCAK) (For Cloud Security)
ISC2 Certified Cloud Security Professional (CCSP) (For Cloud Security)
Pre-course instructions
Hardware & Software:
This course will be conducted as a Virtual Live Class (VLC) via Zoom platform.
Participants must own a Zoom account and have a laptop or a desktop with “Zoom Client for Meetings” installed. Download from zoom.us/download.
Must-have:
Please ensure that your computer or laptop meets the following requirements.
Operating system: Windows 10 or MacOS (64 bit or above)
Processor/CPU: 1.8 GHz, 2-core Intel Core i3 or higher
Minimum 20 GB hard disk space
Minimum 8 GB RAM
Webcam (camera must be turned on for the duration of the class)
Microphone
Internet Connection: Wired or Wireless broadband
Latest version of Zoom software to be installed prior to the class
Good-to-have:
Wired internet connection: Wired internet will provide you with stable and reliable connection.
Dual monitors: Using a dual monitor setup will improve your training experience, enabling you to participate in hands-on exercises and maintain engagement with your instructor.
Not recommended:
Using tablets is not recommended due to smaller screen size, which could cause eye strain and discomfort during the program.

Schedule
End Date: 31 Dec 2026, Thursday
Weekdays, Weekends
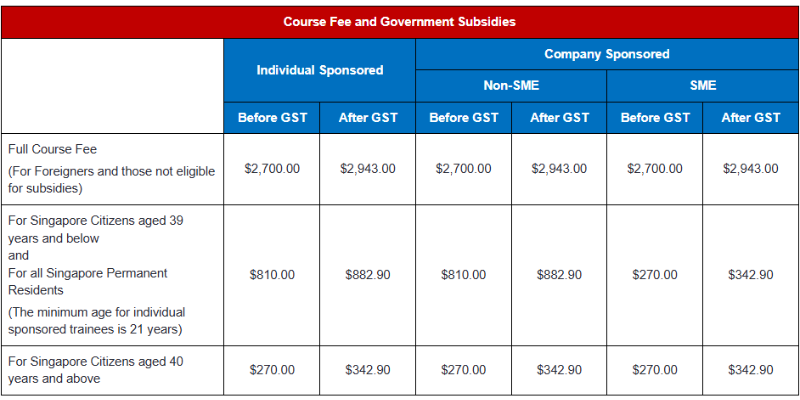
Location: NTUC Trade Union House, 189556 and OnlinePricing
Course fees: SGD 2700 before GST and subsidies
Skills Covered
PROFICIENCY LEVEL GUIDE
Beginner: Introduce the subject matter without the need to have any prerequisites.
Proficient: Requires learners to have prior knowledge of the subject.
Expert: Involves advanced and more complex understanding of the subject.
- Cybersecurity (Proficiency level: Proficient)